Advances in technology are being embraced by both security teams protecting sensitive corporate data and the sophisticated criminals trying to disrupt business. Addressing security, privacy and compliance concerns are often cited by businesses as top priorities before adopting Cloud or BYOD technologies. As a member of and advisor to Wisegate, I partnered with the IT advisory service to survey over a hundred security leads to learn what’s most important to CISOs, what innovations they’re focused on to address their most pressing problems, and how they’ re planning to help businesses take smart risks.
Key findings:
- New battlefields, same war. CISOs remain vigilant on the fundamentals – Malware Outbreaks and Data Breaches. Security teams confront growing risks on many fronts, from new technologies to external threat factors. Driving their security strategies are 6 technology trends and 5 top risks.
- Security programs prioritize risks and business alignment, but lack tools to draw the big picture. Their risks are increasing, but only half can efficiently report risk status to their Boards and internal business partners.
- As IT hands off infrastructure control, CISOs focus on the data. Shared risk models – a nod to the expanding universe of user devices and the dissolving enterprise perimeter.
- Automate all the things. CISOs push automation, orchestration to manage point solution sprawl. Consolidation and automation are top areas of focus to improve security program maturity. Three-quarters of CISOs are building or integrating solutions to address their top risks. APIs are frequently requested features in modern security solutions.
1. Tech Trends and Risks Driving Security Programs
Six Top Technology Trends
Businesses are embracing and realizing the productivity benefits of BYOD, Everything as a Service, and ubiquitous connectivity from their mobile devices. One of the consequences of these shared-risk models is losing visibility and manageability on endpoints, applications, and networks. These advances have impaired traditional security controls based on traffic inspection, blacklist signature-matching, and device management. Businesses have accepted these risks in exchange for their benefits, driving innovation for alternative solutions to secure corporate data. Advances in predictive and behavioral analytics, Cloud Application Security Brokers and SecDevOps methodologies, for example, help security teams remain effective at addressing their top risks — harmful applications and the loss of sensitive corporate data.
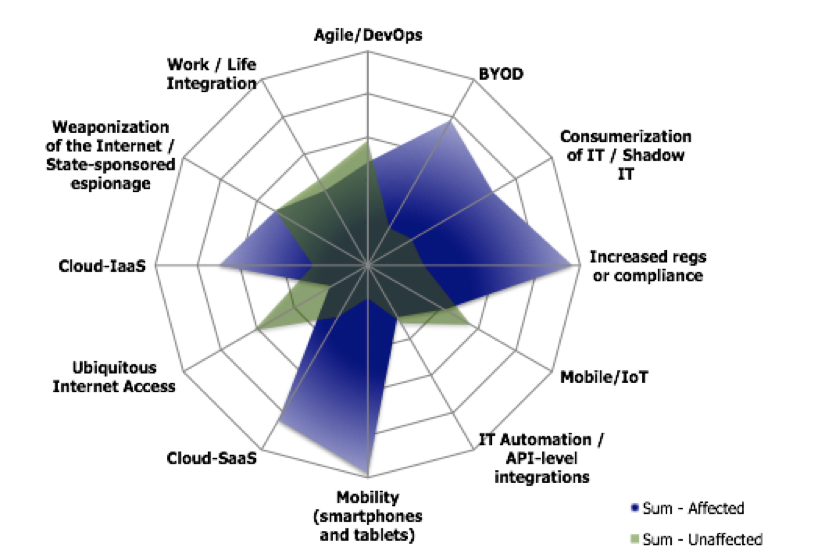
Five Top-Of-Mind Risks
Five risks capture 51% of CISOs’ top concerns, and are increasing industry-wide. Two risks in particular – Malware Outbreak and Sensitive Data Breach – account for nearly 1/3 of all CISOs’ attention. They were more important to participants than the next 6 identified risks combined. Beyond the top half, risk priorities quickly become diffuse and follow a power-law curve – indicating that security priorities differ across industries, companies, and program maturities. See our earlier post for a “word cloud” version of top risks.
Although Malicious Insider Threats receive a lot of press and are harder to detect, external threat actors pose a greater overall concern. Verizon’s 2014 Data Breach Incident Report indicates that only 8% of reported data breaches involved malicious insiders. Our data suggests that although the “insider threat” is a concern, it’s not in participants top-3. Coincidentally, behavior-based controls show promise at detecting anomalies in both endpoint application execution and activity logs — we look forward to more innovations in both of these top-risk areas.
2. Prioritizing Security Programs, Measuring Their Impact
Risk-Based, Business-Aligned Programs
With so many possible ways for harm to affect a company and its data, how do information security programs prioritize what to focus on, what threats should teams address first, and when should they change their focus? Teams overwhelmingly follow “Risk-Based” approaches, and look forward about 2 years when reviewing their strategic roadmaps. As security products themselves implement more cloud-based controls (either directly or embedded within vendor products), security teams will stay agile amidst ever-evolving threats.
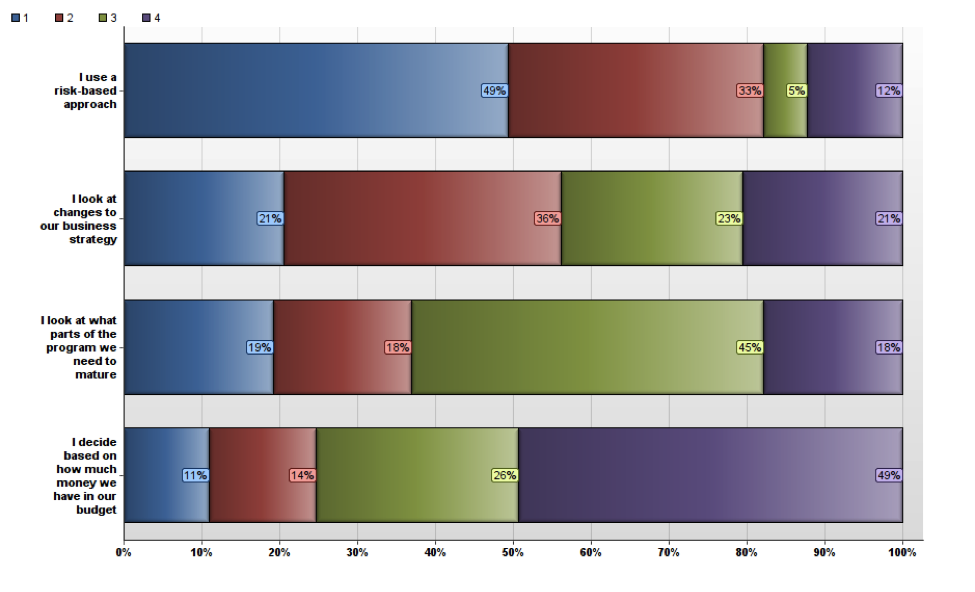
Q: How do you prioritize your security program?
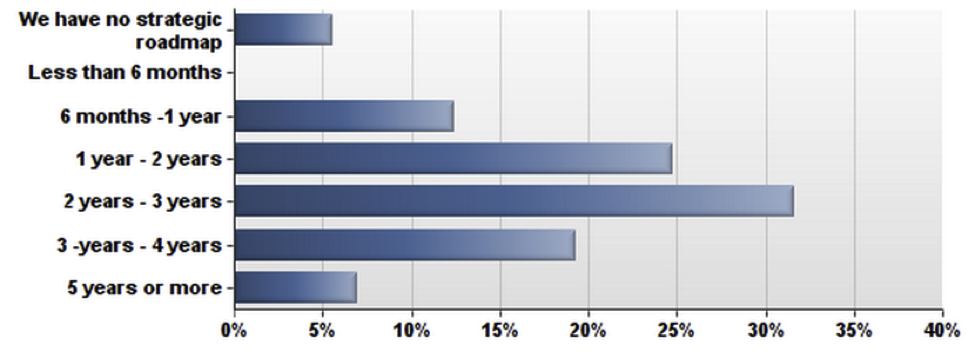
Q: How far out do you plan your strategic roadmap?
But Metrics and Reporting Impact Are Lacking
Despite being able to identify their top risks, one-half of our participants admitted they didn’t have good ways to measure the status of these risks or how effective their programs were at address them. This is surprising and concerning – imagine trying to fly an airplane at night with your three most important cockpit indicators missing.
Security and risk management systems are becoming Board-level discussions, government and industry regulations are also requiring better risk monitoring and controls. While many security products do provide dashboards, those tend to be specific to that product’s threats and activities. What’s needed are efficient ways to map all of this event data into holistic, business-level perspectives.
3. Data-centric Enterprise Security Programs
CISOs are looking to put security controls as close as possible to enterprise data, versus focusing on specific device types or threats. Information Protection and Control products ( “IPC” , including DLP/DRM/masking/encryption technologies) were the #1 desired control to apply on computers, at the infrastructure layer, within applications, and on Mobile endpoints.
Data-centric security will become increasingly important as emerging “Cloud Always” companies implement modern enterprise stacks, established enterprises refresh their technologies with “Cloud First” initiatives, and even “Cloud Cautious” companies realize the benefits of SaaS and IaaS. By focusing on capabilities and adherence to data-centric security controls instead of specific device types, security teams can support a wider range of BYOD endpoints and applications. Storing and processing corporate data within SaaS and PaaS providers becomes less risky if the enterprise manages the encryption keys. There are many operational considerations to address, such as enterprise search and key distribution, but this is a promising area to address a wide range of risks.
4. Automating, Integrating Controls to Stay Secure
Security teams are consolidating and automating their controls
- Over half (59%) marked as a top-choice proactive threat/misuse detection or automated orchestration to streamline their incident response processes.
- Three-quarters needed to build a custom solution or integration to address their top risk.
- Almost one-third (31%) are prioritizing security controls for DevOps environments. I also spoke about this in CSO Magazine.
- Aside from two participants planning to turn down their AntiVirus systems, security teams keep adding additional controls to their programs as new threats emerge.
And finally, several participants remarked that they’re concerned about managing an ever-expanding set of security point solutions. Even if security teams could easily find qualified staff to run new controls, they get better efficiencies driving security initiatives via automation and APIs. This is consistent with our investment in Chef and the notion that good security posture is based on solid operational controls and consistent configuration management.
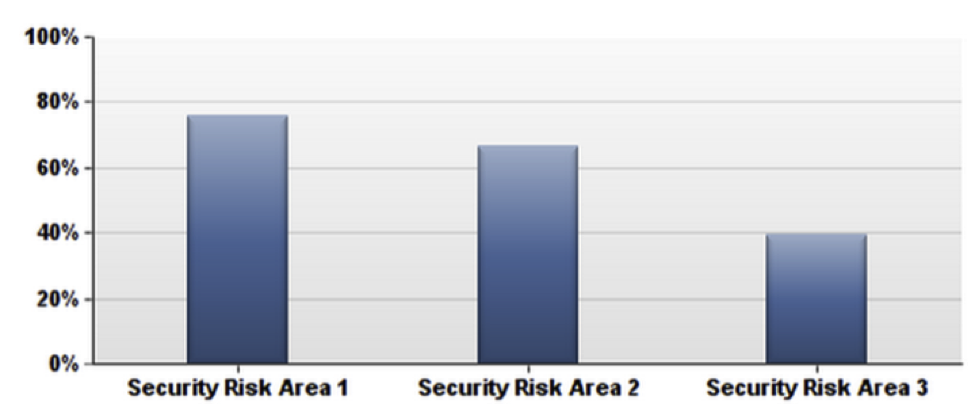
Q: For which risks did you need to build something in-house because there were no acceptable commercially available alternatives?
Methodology
We met with nearly two-dozen CISOs across more than 15 industries, asking about trends, externalities, and what they’re focusing on to protect their enterprise risks. We then partnered with Wisegate who surveyed their members to get a broader, in-the-trenches perspective on security practices and strategies. This increased our total, usable sample size to just over 100.
There was strong consistency between both data sets and we saw some “spreading” amongst priorities, implying that both program maturity and product choice is alive and well within the Information Security market. We also collected attributes about InfoSec programs and heard glimpses of what makes security programs successful. I will be presenting more details on these findings at the Gartner Catalyst Conference in San Diego August 11, 2014.
We hope these findings are helpful to both enterprise security teams and security startups contemplating new approaches. We’d like to thank our CISO survey participants for their time and insights, and Wisegate for their expertise. Future InfoSec opportunities are large, defenders are eager to gain new capabilities, and the market is ready for new innovations to disrupt the status quo.