InfoSec Uncovered: Exploring the mind of the CISO
During this past quarter our current EIR and security expert Bill Burns has been researching and building an investment thesis around the enterprise Information Security space.
We set out to determine which social and technological trends most affect information security programs, and how security organizations protect their corporate and customer information as companies evolve and adapt to these trends. We also wanted to see what changes in the threat landscape are impacting InfoSec teams and what perceived market gaps exist – e.g. problems without good solutions. It’s not uncommon for security to lag behind technology innovations, and different organizations have different risk appetites, budgetary constraints, and regulatory mandates. All of these factors affect how teams manage security and risk within a particular organization, and create opportunities for innovative startups.
I’m excited to share some of Bill’s early results and give back to the security community that has helped us so graciously with their time and insights.
Giving CISOs a chance to nudge the security marketplace
To understand what market forces are at play within the security space, we reached out to nearly two-dozen CISOs across 15 industries. We wanted to know how their security programs are maturing and being disrupted, how effective CISOs are at dealing with substantial changes to their attack surface and sets of controls, and we wanted to know what “keeps them up and night” and how they’re meeting that challenge. What we heard in these interviews was refreshingly candid and insightful. They shared what controls are working, where they see concern and opportunities ahead, and what they’re strategically focused on going forward.
What Keeps CISOs Up At Night?

Regarding these top-of-mind risks, the consensus was that teams want to approach security more as a “science” as less as an “art”. Security organizations were looking to:
- automate, standardize and manage their most important assets in their organization
- find systematic ways to respond to changes in the ecosystem, integrate their solutions together and have the tools make sense of the data they already are getting
- build baselines of what’s “normal” to, hopefully, discover earlier when things are “abnormal” and require more thorough analysis
We also asked CISOs to identify external forces most likely to affect their security program strategy in the near future. It’s not surprising that Mobile Computing, and Cloud technologies (both SaaS and IaaS) were top security forcing functions, since they’re also top-of-mind for CIOs and organizations to improve employee productivity. Increases in Regulatory/Compliance pressure also ranked highly.
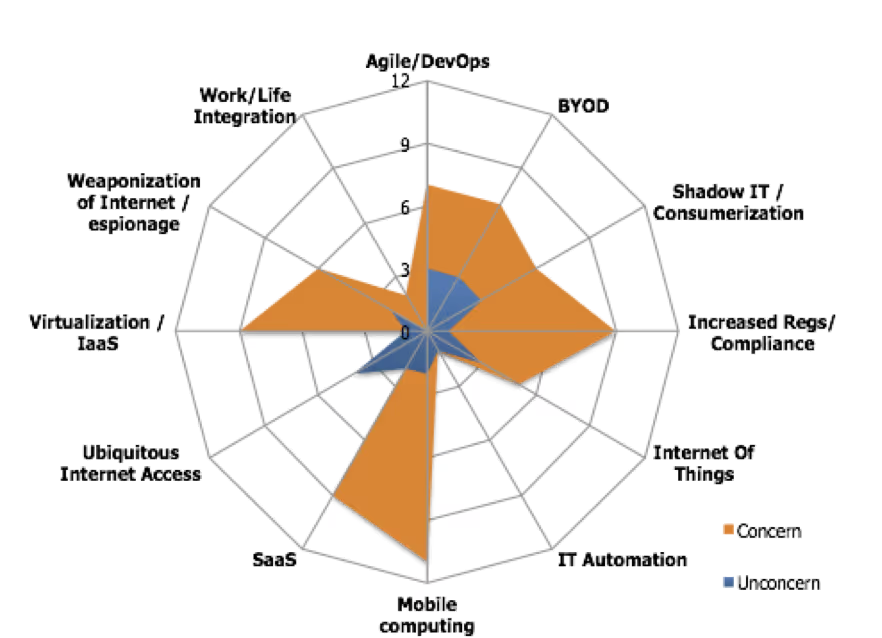
Securing Agile / DevOps methodologies also was top-of-mind for CISOs, which is encouraging. Our investment in Chef has shown that enterprises are adopting automation rapidly, and it’s great to see security teams embracing this trend to deploy security controls more consistently and continuously. We anticipated going into the research, and the participating CISOs confirmed, that automation and API-level access will become table stakes for security products going forward, to support a new level of interoperability and customization.
The use of BYOD and “Shadow IT” also scored as top concerns for many participants. These two technologies are managed by end-users, which causes concern for those typically assigned to protect the data being processed and managed. Data breach reports such as Verizon’s seminal Data Breach Investigation Report and post-mortems from high-profile incidents frequently implicate poor security controls on endpoints and attackers socially engineering persons to infiltrate companies and exfiltrate their data.
- The concern from CISOs over BYOD was around usability vs. protection. Applying traditional enterprise security controls on a consumer device frequently affects the “consumer” experience that makes BYOD so popular in the first place. The CISOs we polled weren’t completely satisfied with the choice of products in this space, so we continue to see opportunity here as companies seek a balance between the need for visibility and protection versus the benefits of supporting innovative devices. In a later post, we’ll cover the divergence between “endpoint security” vs. “network security” – there was no clear winner-take-all approach articulated by participants. If your company is working on a better BYOD mousetrap, we’d like to hear from you!
- And finally, Shadow IT is still seen as a challenge for Information Security teams to manage. Security teams are still concerned how best to effectively strike the right balance between monitoring for risky behaviors, blocking “unsanctioned” applications, and maintaining regulatory compliance…while adopting the efficiencies inherent with SaaS cloud applications. The good news is that there are many choices in this space, the problem is choosing which product has the specific feature set you need. Eventually some consolidation is likely in this space since many of the CISOs we spoke to wanted key features from multiple vendors.
We also measured trends that have the least effect on security priorities, and those were more industry-specific. What matters least to a highly-regulated government contractor (that can afford to lock down or prohibit BYOD) is different from a fast food restaurant chain that doesn’t write custom applications. Choice is alive and well within the information security market!
What’s next?
We’ve just scratched the surface on the insights we’ve gleaned from our initial survey. We’ve partnered with Wisegate, a next generation IT advisory company, to create a streamlined version of this security questionnaire and open it up to a broader audience. For more information on Wisegate and a to see a list of their community-based public reports, please visit here.
Bill shared some of early insights last month at the Rocky Mountain Information Security Conference. We’ll be sharing more of these research results this quarter as this research project wraps up, including the security market segments that we find most interesting. Stay tuned!
News from the Scale portfolio and firm